(DES) Data Encryption Standard
🔐 Unlocking DES: The Algorithm that Shaped Modern Encryption! 🔐
Ever wondered how your sensitive data was first locked away from prying eyes? Enter the Data Encryption Standard (DES) – the 1977 cryptographic superstar that set the gold standard for data security!
DES took plaintext, diced it up, and spun it through 16 powerful rounds of confusion and diffusion, transforming it into impenetrable ciphertext. With its 56-bit key and Feistel network wizardry, DES wasn’t just an encryption algorithm – it was a blueprint for the future.
But like all stars, DES began to fade. As computing power surged, so did hackers’ abilities to crack its short keys. By the late 90s, brute-force attacks spelled the end for DES, making way for the next-gen AES (Advanced Encryption Standard).
Despite its retirement, DES’s legacy lives on. Its design principles still echo in today’s cryptography, proving that even legends never truly die.
🔍 Want to dive deeper into the DES mechanism, strengths, and vulnerabilities? Let’s decrypt the story behind one of the most iconic encryption algorithms ever!
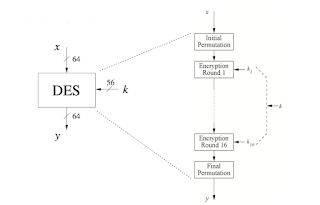
Data Encryption Standard
• Key Length: DES uses a 56-bit key, although the key is typically input as a 64-bit value, with every eighth bit used for parity.
• Key Schedule: The key is divided into two 28-bit halves, which are then shifted and permuted to create 16 subkeys (one for each round of encryption).
• Before the main rounds of processing, the 64-bit block of plaintext undergoes an initial permutation that rearranges the bits according to a fixed table.
• DES consists of 16 rounds of processing. Each round includes:
• Expansion: The right half of the data block (32 bits) is expanded to 48 bits using an expansion permutation.
• Key Mixing: The expanded right half is XORed with the round key.
• Substitution: The result is divided into eight 6-bit segments, each of which is passed through a substitution box (S-box) that transforms it into a 4-bit output.
• Permutation: The outputs from the S-boxes are permuted using a fixed permutation (P).
• Swap: The left and right halves of the block are swapped after each round, except after the final round.
• After the 16 rounds, the final output undergoes a final permutation, which is the inverse of the initial permutation.
• Decryption in DES is similar to encryption but involves applying the subkeys in reverse order.
• Input: 64-bit plaintext
• Output: 64-bit ciphertext
• Rounds: 16
• Key Size: 56 bits
• Block Size: 64 bits
Feistel Structure
The Feistel structure is a symmetric encryption algorithm design that divides the input data into two halves and processes them through multiple rounds of transformation. In DES, the plaintext is split into two 32-bit halves (left half L and right half R). Each round consists of:
1. Function Application: The right half R is expanded and transformed using a round function F, which incorporates the round key.
2. XOR Operation: The output of the function F is XORed with the left half L.
3. Swap: After processing, the left and right halves are swapped for the next round, except after the last round.
This structure allows for complex transformations while still being reversible, which is essential for decryption.
The Initial Permutation (IP) is the first step in the DES encryption process. It rearranges the bits of the plaintext block according to a fixed table. The purpose of IP is to provide an initial diffusion of the input data, making it harder to analyze patterns in the plaintext.
• Input: 64-bit plaintext block.
• Output: Permuted 64-bit block.
• Effect: The specific rearrangement of bits does not add security by itself but helps in spreading out the bits for subsequent processing.
The Final Permutation (FP) is the last step in the DES encryption process, occurring after all rounds of processing. It is essentially the inverse of the initial permutation.
• Input: The output from the last round of processing (which consists of two 32-bit halves).
• Output: 64-bit ciphertext.
• Effect: The FP rearranges the bits back into a specific order, ensuring that the output format matches that of the input format, thus completing the encryption process.
F Function
The F function is a key component of DES, taking a 32-bit data half (typically the right half, R) and a 48-bit round key. It performs the following operations:
1. Expansion: The 32-bit R is expanded to 48 bits through an expansion permutation, enhancing diffusion.
2. Key Mixing: The expanded R is XORed with the 48-bit round key Kᵢ.
3. Substitution: The result is divided into eight 6-bit segments, each passed through an S-box that maps it to a 4-bit output.
4. Permutation: The output from the S-boxes is rearranged using a fixed permutation (P-box).
The output of the F function is then used in the Feistel structure for further processing.
Key Schedule
The key schedule generates the round keys for each of the 16 rounds of DES:
1. Key Input: DES uses a 64-bit key, but only 56 bits are utilized after discarding parity bits.
2. Key Permutation (PC-1): The 56-bit key undergoes an initial permutation to rearrange bits.
3. Splitting: The permuted key is split into two 28-bit halves, C₀ and D₀.
4. Key Rotation: Each half undergoes left rotation (1 or 2 positions) for each round.
5. Key Selection (PC-2): After rotation, a selection permutation creates a 48-bit round key Kᵢ.
the F function mixes data and key information, while the key schedule generates unique round keys for enhanced security in each encryption round.
Strengths and Weaknesses of DES
Strengths of DES:
1. Simplicity and Speed: DES is relatively straightforward to implement, making it efficient for hardware and software applications. Its structure allows for fast encryption and decryption processes.
2. Established Security: When it was introduced in the 1970s, DES was considered secure and widely adopted, forming the foundation for many cryptographic protocols and standards.
3. Block Cipher Design: DES operates on fixed-size blocks (64 bits), which is a common design in cryptography. This uniformity simplifies many aspects of encryption and data handling.
4. Feistel Structure: The Feistel network design used in DES allows for easy implementation of the decryption process, as the same algorithm can be used for both encryption and decryption with different keys.
Weaknesses of DES:
1. Key Length: The primary weakness of DES is its 56-bit key length, which is now considered inadequate against modern computational power. With advancements in technology, brute-force attacks can be executed relatively quickly.
2. Vulnerability to Cryptanalysis: Over time, various cryptanalysis techniques have been developed that can exploit patterns in DES, such as differential and linear cryptanalysis. These methods can significantly reduce the effective security of the cipher.
3. Limited Security Margin: As computing power continues to grow, the security margin of DES diminishes. The increasing feasibility of exhaustive search attacks makes it less secure over time.
4. Obsolescence: Due to its vulnerabilities and the advent of stronger algorithms like AES (Advanced Encryption Standard), DES is largely considered obsolete for protecting sensitive information today.
Conclusion
In conclusion, while the Data Encryption Standard (DES) played a pivotal role in the evolution of cryptography and established foundational principles for secure data transmission, its weaknesses—primarily stemming from its short key length and susceptibility to modern attack methods—have rendered it inadequate for contemporary security needs.
As we move forward in an era where data breaches and cyber threats are increasingly prevalent, it is crucial to adopt stronger encryption standards like AES, which provide enhanced security features and resilience against current cryptographic attacks. Understanding the strengths and weaknesses of DES not only highlights its historical significance but also underscores the importance of evolving our security practices in line with technological advancements. Thank you!




Comments
Post a Comment